The easiest way to set up own Jitsi meet server is containerization (see Jitsi in docker).
When you would like to change logo watermark you can use this method. It will work only in this instance of docker. You can stop / start container, but when you destroy it (i.e.: docker-compose down) the changes will gone.
Copy new file (original dimensions are 612x272) to your docker server and place in directory:
~/.jitsi-meet-cfg/web/
check id / name of your web container, i.e.:
[docker@docker jitsi-meet]# docker-compose ps
Name Command State Ports
------------------------------------------------------------------------------------------------
jitsi-meet_jicofo_1 /init Up
jitsi-meet_jvb_1 /init Up 0.0.0.0:10000->10000/udp, 0.0.0.0:4443->4443/tcp
jitsi-meet_prosody_1 /init Up 5222/tcp, 5269/tcp, 5280/tcp, 5347/tcp
jitsi-meet_web_1 /init Up 0.0.0.0:8443->443/tcp, 0.0.0.0:8000->80/tcpas you can see in my case it is the jitsi-meet_web_1.
Execute bash inside container:
docker exec -it jitsi-meet_web_1 /bin/bash
replace original watermark
cd /usr/share/jitsi-meet/images/ mv watermark.png watermark.png-old cp /config/new-logo.png watermark.png
it's not necessary, but I've saved Jitsi watermark as watermark.png-old.
That's all.
You can also check ~/.jitsi-meet-cfg/web/interface_config.js file for other parameters.
Nowadays everybody use some conferencing systems. If you would like to have your own, on controlled infrastructure, maybe only in LAN/VPN environment you can try Jitsi.
The "demo" installation in CentOS 7 based on docker containers is quite simple.
Install docker and docker-compose
If you already have docker installed skip this step. You can also read Docker in CentOS 7 in 5 steps.
curl -fsSL https://get.docker.com/ | sh systemctl start docker systemctl enable docker curl -L "https://github.com/docker/compose/releases/download/\ 1.23.1/docker-compose-$(uname -s)-$(uname -m)" \ -o /usr/local/bin/docker-compose chmod +x /usr/local/bin/docker-compose
Prepare environment
Install GIT
yum install git
Download docker files
git clone https://github.com/jitsi/docker-jitsi-meet && cd docker-jitsi-meet
Prepare directories
mkdir -p ~/.jitsi-meet-cfg/{web/letsencrypt,transcripts,prosody,jicofo,jvb}
cp env.example .env
Needed modifications
If you want to use it in LAN/separated network you have to change
DOCKER_HOST_ADDRESS=192.168.1.89 JVB_STUN_SERVERS=
in .env file. Of course DOCKER_HOST_ADDRESS will be YOUR docker IP address.
If you not set JVB_STUN_SERVERS to null value you won't be able to join the conference. You can change it later in
~/.jitsi-meet-cfg/jvb/sip-communicator.properties file.
Configure firewall
cat <<EOF > /etc/firewalld/services/jitsi.xml <?xml version="1.0" encoding="utf-8"?> <service> <short>Jitsi</short> <description>Multi-platform open-source video conferencing system</description> <port protocol="tcp" port="8000"/> <port protocol="tcp" port="8443"/> <port protocol="tcp" port="4443"/> <port protocol="udp" port="10000"/> </service> EOF firewall-cmd --reload firewall-cmd --add-service jitsi firewall-cmd --permanent --add-service jitsi
Start all
docker-compose -f docker-compose.yml -f etherpad.yml up -d
As you can see I've also added etherpad - for document sharing.
First of all you should prepare image with LDAP support as described in Docker image of Wordpress with LDAP support or why do not use ldap plugin before you created container...
But if you already have a container there is also possibility to enable LDAP support:
Run bash inside container:
docker exec -it wordpress_wordpress_1 /bin/bash
then exec:
apt-get update apt-get install -y libldap2-dev docker-php-ext-configure ldap --with-libdir=lib/x86_64-linux-gnu/ docker-php-ext-install ldap rm -rf /var/lib/apt/lists/* apt-get purge -y --auto-remove libldap2-dev /etc/init.d/apache2 restart
the last line will terminate container. If you have set power policy to restart always there is nothing you have to do. Alternatively you can run container again
docker start wordpress_wordpress_1
Install docker
curl -fsSL https://get.docker.com/ | sh
start, and enable to start after rebooting:
systemctl start docker systemctl enable docker
optionally you can add permissions you yourself:
usermod -aG docker jaqb
in my case my user is jaqb.
Install docker-compose
curl -L "https://github.com/docker/compose/releases/download/\ 1.23.1/docker-compose-$(uname -s)-$(uname -m)" \ -o /usr/local/bin/docker-compose chmod +x /usr/local/bin/docker-compose
you have to check if there is newer version than 1.23.1.
Install kubectl:
cat <<EOF > /etc/yum.repos.d/kubernetes.repo [kubernetes] name=Kubernetes baseurl=https://packages.cloud.google.com/yum/repos/kubernetes-el7-x86_64 enabled=1 gpgcheck=1 repo_gpgcheck=1 gpgkey=https://packages.cloud.google.com/yum/doc/yum-key.gpg https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg EOF yum install -y kubectl
Install Minikube:
curl -LO https://storage.googleapis.com/minikube/releases/latest/minikube-linux-amd64 install minikube-linux-amd64 /usr/local/bin/minikube
It copy file minikube-linux-amd64 to /usr/local/bin/minikube.
Install docker:
curl -fsSL https://get.docker.com -o get-docker.sh bash get-docker.sh
downgrade to supported version:
yum remove docker-ce docker-ce-cli yum install docker-ce-18.06.1.ce systemctl enable docker systemctl start docker
Set hostname
You have to have name minikube be resolved to your IP:
hostname minikube
Optional
Install conntrack:
yum install conntrack
Installing crictl:
VERSION="v1.12.0" curl -LO https://github.com/kubernetes-sigs/cri-tools/releases/download/$VERSION/crictl-$VERSION-linux-amd64.tar.gz tar zxvf crictl-$VERSION-linux-amd64.tar.gz -C /usr/local/bin rm -f crictl-$VERSION-linux-amd64.tar.gz
Recomended settings:
iptables -I INPUT -p tcp --dport 8443 -j ACCEPT iptables -I INPUT -p tcp --dport 10250 -j ACCEPT swapoff -av
The main command:
minikube --vm-driver=none start
you should get something like this:
Starting local Kubernetes v1.10.0 cluster...
Starting VM...
Getting VM IP address...
Moving files into cluster...
Downloading kubelet v1.10.0
Downloading kubeadm v1.10.0
Finished Downloading kubeadm v1.10.0
Finished Downloading kubelet v1.10.0
Setting up certs...
Connecting to cluster...
Setting up kubeconfig...
Starting cluster components...
Kubectl is now configured to use the cluster.
===================
WARNING: IT IS RECOMMENDED NOT TO RUN THE NONE DRIVER ON PERSONAL WORKSTATIONS
The 'none' driver will run an insecure kubernetes apiserver as root that may leave the host vulnerable to CSRF attacks
When using the none driver, the kubectl config and credentials generated will be root owned and will appear in the root home directory.
You will need to move the files to the appropriate location and then set the correct permissions. An example of this is below:
sudo mv /root/.kube $HOME/.kube # this will write over any previous configuration
sudo chown -R $USER $HOME/.kube
sudo chgrp -R $USER $HOME/.kube
sudo mv /root/.minikube $HOME/.minikube # this will write over any previous configuration
sudo chown -R $USER $HOME/.minikube
sudo chgrp -R $USER $HOME/.minikube
This can also be done automatically by setting the env var CHANGE_MINIKUBE_NONE_USER=true
Loading cached images from config file.
Launch first pod:
kubectl run hello-minikube --image=k8s.gcr.io/echoserver:1.10 --port=8080 kubectl run --generator=deployment/apps.v1beta1 is DEPRECATED and will be removed in a future version. Use kubectl create instead. deployment.apps/hello-minikube created kubectl expose deployment hello-minikube --type=NodePort service/hello-minikube exposed
check if it works:
kubectl get pod NAME READY STATUS RESTARTS AGE hello-minikube-7c77b68cff-677z8 1/1 Running 0 3m
you can also check ip or service url:
minikube ip minikube service hello-minikube --url
when you check that it works (using browser/wget/culr) you can cleanup:
kubectl delete services hello-minikube kubectl delete deployment hello-minikube
but what is it for...?
I've upgraded Pi-hole do 4.0 version:
docker run -d --name pihole-4.0.0-1 \
--dns 127.0.0.1 --dns 1.1.1.1 \
-e ServerIP=192.168.1.28 -e DNS1=192.168.1.4 \
-e WEBPASSWORD=secret \
-p 8018:80 -p 53:53 -p 53:53/udp \
--restart=unless-stopped \
pihole/pihole:4.0.0-1
as you can see I use new name (pihole/pihole), set power policy and additional --dns option - it's necessary.
Last time I've to manually edit /etc/resolve.conf inside container - this is simple workaround.
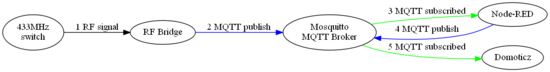
How to switch light using 3 channels 433MHz switch. It's very simple:
1 RF signal
My 3 button 433MHz switch sends 3 codes:
- 672BE2- left button
- 672BE8 - center button
- 672BE4 - right button
2 MQTT publish
I set up RF Bridge to send MQTT messages like this (center button):
{
"RfReceived" : {
"Sync" : 7840,
"Low" : 250,
"High" : 780,
"Data" : "672BE8",
"RfKey" : "None"
}
}
to topic:
tele/DVES_B2EFB9/RESULT
Domoticz needs to get mesage with topic:
domoticz/in
with payload like this:
{
"idx" : 22,
"command" : "switchlight",
"switchcmd" : "Toggle"
}
We need to translate:
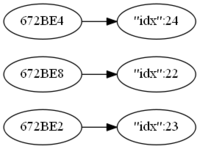
3, 4 and 5 message translation
Mosquitto and Node-RED are deployed using Docker on same machine:
docker run -it -p 1883:1883 -p 9001:9001 --name mosquitto \ -v mosquitto:/mosquitto/config -v mosquitto:/mosquitto/data \ -v mosquitto:/mosquitto/log eclipse-mosquitto docker run -d -p 1880:1880 --restart=always \ --log-opt max-size=10m --log-opt max-file=5 \ -v node-red-data:/data --name nodered \ --link mosquitto:broker nodered/node-red-docker:slim
You can see that I've link mosquitto container as broker.
The switch node splits messages depending on msg.payload.RfReceived.Data, and change node set properties (idx, command and switchcmd)
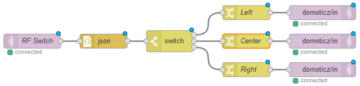
Here you have complete Node-RED code.
Finally Domoticz tuns the light!
Of course you have to have set up Domoticz first.
If you forgot to set-up power policy during container creation you can easy modify it:
docker update --restart=always my-container
you can check it:
docker@docker:~$ docker inspect my-container | grep -A3 "RestartPolicy"
"RestartPolicy": {
"Name": "always",
"MaximumRetryCount": 0
}, If you use ReadyNAS OS 6 you can install Pi-hole in Docker container:
docker run --name my-new-pi-hole \
-e ServerIP=191.168.1.28 \
-e DNS1=192.168.1.4 \
-e WEBPASSWORD=secret \
-d \
-p 8080:80 -p 53:53 -p 53:53/udp \
diginc/pi-hole
you don't have to run
docker pull diginc/pi-hole
it will be done automatic (or rather automagic).
As You can see I've set up several parameters:
- run is command to docker to run container
- --name my-new-pi-hole is name of container (optional)
- -e means Environment Variable - it is to pass some options to container
- ServerIP - it is IP that Pi-hole should use (mandatory)
- DNS1 - IP of your DNS server (optional) - if you not provide it will use google's DNS
- WEBPASSWORD (useful) - you will need it to login to administration portal
- -d - tells to docker that this container should work in background
- -p - is port redirection from your docker machine to port in container
- 8080:80 (useful) - is redirection of 8080 port of your docker machine to port 80 in container
- 53:53 (optional)- is redirection of 53 port of your docker machine to port 53 in container (not necessary in my case)
- 53:53/udp (very useful) - is the same for UDP port - this is what we need to work
- diginc/pi-hole - is of course name of image to run
Now you can use command
docker ps
to get some information about your container
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 891aeb2c127b diginc/pi-hole "/s6-init" 7 seconds ago Up 2 seconds (health: starting) 0.0.0.0:53->53/tcp, 0.0.0.0:53->53/udp, 0.0.0.0:8080->80/tcp my-new-pi-hole
as you can see status is health: starting, after some time it will change to healthy.
Now you can login to (192.168.1.28 is address of may docker machine) http://192.168.1.28:8080/admin/ to check that no one has used your server (Total queries 0).
Let's check if it works:
root@mynas:~# host jaqb.gda.pl 192.168.1.28 Using domain server: Name: 192.168.1.28 Address: 192.168.1.28#53 Aliases: jaqb.gda.pl has address 185.204.216.106 jaqb.gda.pl mail is handled by 0 mail.jaqb.gda.pl.
Yes!
Now it's enough to change default DNS in your LAN to your docker machine (in my case 192.168.1.28).

Add comment